What Is Phishing? Your Guide to Staying Safe
Phishing scams target crypto users through fake emails, websites, and messages. Learn how to identify and protect yourself from these cyber threats.

Did you know that last year, the Anti-Phishing Working Group, APWG reported a total of 1,270,883 total phishing attacks and 23.2% were targeted at the financial sector?
Phishing is one of the most common online scams people fall for, and this article explains the different methods of phishing attacks and what to do if you've been a target.
What is Phishing?
Phishing is when cybercriminals try to deceive you into believing they are a trustworthy person, agent or company representative by sending you emails, texts, or calling you on the phone.
Their aim is to persuade you to provide them with private information like your email password, bank account details, or credit/debit card information.
Once they get this confidential information, they can steal money from your crypto wallet and bank account or steal your identity.
What methods are used to conduct phishing attacks?
Here are five popular ways cybercriminals and hackers conduct phishing attacks:
1. Phishing through Fake Links or Documents Attached to An Email
One of the oldest and most common ways cybercriminals target users is by attaching documents or website links to an email. Hackers know that most people don't confirm or cross-check the validity of an email before clicking on an attached link or document.
The document could look like an invoice, an email delivery failure message or even a flight confirmation message. The website links could appear to direct you to change your password, follow up with a team member, or contact a business partner.
Whatever the format, these links and documents are faked to deceive you into clicking them. Once you click, your online security is immediately in danger, and your sensitive information is on its way to being used against you.
2. Spear Phishing
Spear phishing happens when fraudulent or fake emails are sent to you with some of your personal information attached, like your job title, full name or house address.
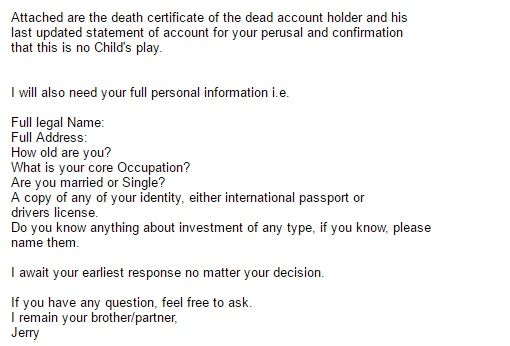
Hackers who use spear phishing target people who share their personal information online. Think about the Twitter question-and-answer threads where people share details about themselves, like their favourite colour, where they grew up, sibling names, jobs, etc. Or Facebook posts showing their location or celebrating their marriage or work anniversaries.
These harmless social media posts are a gold mine for cybercriminals. They can use it to find your location, spending habits, daily routines and contact information.
Once they have enough data, they will send you an email using your personal details to gain your trust and direct you to a website where you may be asked to enter your bank pin, account number, private wallet key, etc.
3. Phishing via Search Engines
Let's say you're searching for where to get affordable shoes on Google. A list of shopping websites pops up, and you find one that offers low-cost shoes.
When you enter your credit or debit card details, the site collects and saves them without your knowledge. A week later, you discover money has been stolen from your account ( and you still don't have the shoes you paid for).
There are also online loan websites that offer users low-interest loans but are disguised as phishing sites to collect your wallet or account information. The internet is full of millions of websites offering "great deals", but remember, if it's too good to be true, it probably isn't true.
4. Phishing through Brand or Celebrity Impersonation
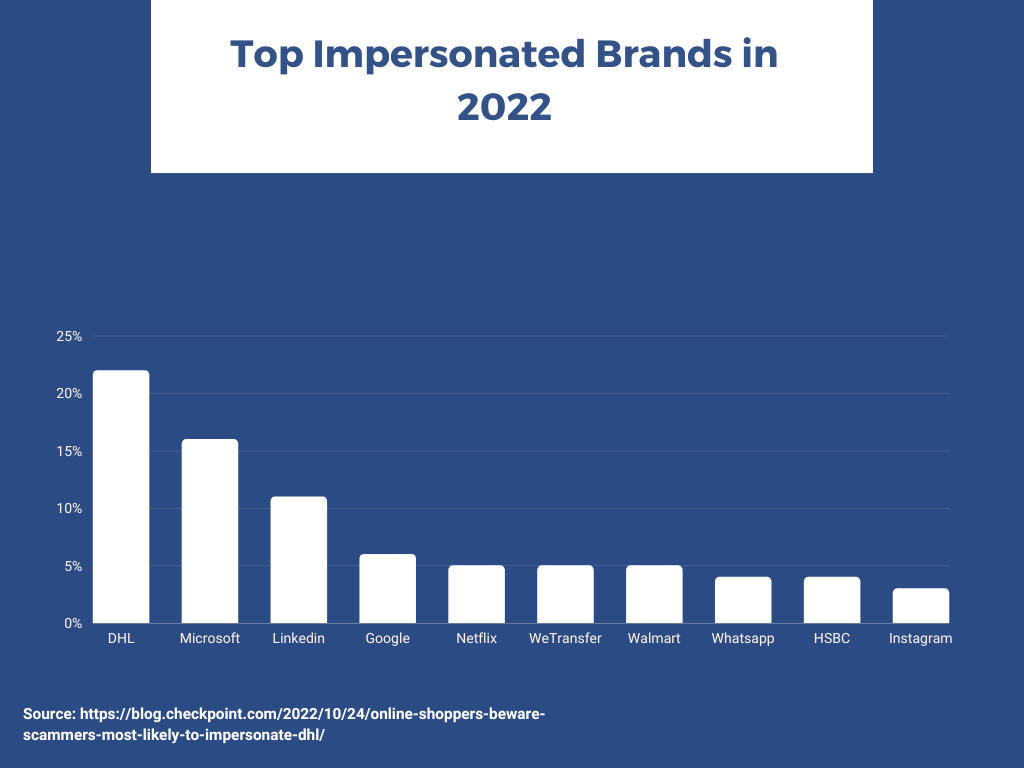
Brand impersonation is an attack that impersonates a trusted company, a brand, or a domain to trick victims into responding and disclosing personal or otherwise sensitive information.
With this type of phishing, a cybercriminal acts like a popular brand or company to trick you into revealing personal or sensitive information. These criminals bank on people trusting the brand name enough not to do any checks to see if the account is credible or not.
For example, a scammer could set up a fake Obiex Twitter, Telegram or Whatsapp account and message you to "resolve a complaint or upgrade your account." Or they could set up a fake celebrity account to convince people to donate money to a fake humanitarian fund or charitable cause.
5. Phishing through Email Account Compromise (EAC) Or Business email compromise (BEC)
EAC/BEC is a high-level phishing scam that generally targets businesses and individuals involved in transferring money or the finance (crypto and fiat) industry. Scammers use fake emails containing links or invoices to target key members of a company or high-ranking individuals. They ensure these emails are professionally written to avoid suspicion.
For example, the hacker could pretend to be a team lead requesting funds transfer from the finance department or a business representative asking a frequent customer to take advantage of a new discount.
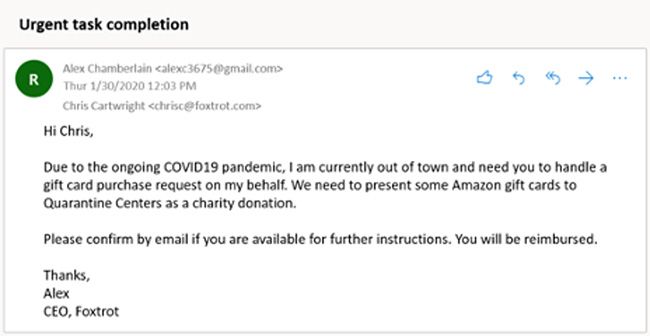
This kind of phishing, also called a Whaling attack, takes advantage of employee willingness to follow instructions from a senior lead, C-suite personnel, and customer trust in a business to infiltrate and steal company funds or clear out an individual's bank account.
How To Recognise Phishing Attacks
It can be difficult to spot a phishing email, especially when they are professionally written and seem to be from brands or individual names you trust. However, these four signs can help you recognise a potential scam email.
1. Emails sent from a public email domain
If the email comes from a public or fake domain, be alert immediately. A public domain email address is one offered by free email service providers like Yahoo, Outlook, Gmail, AOL, etc.
Most companies and brands have their own company email domain. For instance, when you receive an email from Obiex, the address will read [email protected] or [email protected]. The company name at the end lets you know it is legit.
2. Emails sent from misspelt email addresses or domain names
Look out for (deliberate) errors like misspelt links, domain names or email addresses.
Scammers also tend to change the letters of the fake site URL to something similar to that of the authentic site, like changing "i" to "1" or "o" to "0". Also, a fake website link will likely not have a tiny lock icon near the URL bar and no "https" that indicate the site is safe to visit and use.
For example, a scammer could set up an 0biex.com or 0b1ex.com site knowing the URL is identical to the original obiex.com site. This applies to email addresses or domain names as well. If you receive an email from [email protected] or [email protected], you are about to be phished, and you should delete the email, block and report the sender.
3. Suspiciously urgent-Sounding emails
Scammers try to trick you by threatening negative consequences if you don't click a link immediately, send information to an email, or open a document.
It's a particularly devious use of mind tricks and human psychology. In today's world, with so many overwhelming tasks, most people may not read the email properly or check the sender's address and will go on to do as the sender asked.
4. Emails that are written with bad grammar
Poor spelling and grammar errors are among the most popular signs of scam emails. Most businesses ensure their external messages and even internal messages are correctly written. Hence, you are unlikely to receive a poorly written email from a company, organisation, or brand.
What do you do if you have been phished?
If you have been phished, the next steps depend on how it happened. Did you click a link, download a document, or enter your card details, password or sensitive information into a website? Did it happen on your work computer or personal mobile phone? However it happened, here are some general steps to take to manage the phishing attack immediately.
1. Change your passwords
If you have gone as far as typing your crypto email or bank account password into a fake website, change that password immediately. If you use that password for other accounts, change them as well. As a matter of fact, you should change your passwords even if you didn't share them with the hacker, just to be on the safe side.
Sometimes, hackers try to use one password to hack into your other accounts because they know most people use one password for several accounts. When changing your passwords, ensure you choose a strong one that is hard to guess.
2. Scan your computer or phone for viruses
If the phishing attack happened on your personal computer or phone, run an anti-virus scan immediately, and ensure all security software is updated.
If it happened on your work computer or device, contact your IT or security team. They can run anti-virus and malware scans to search the company network for breaches. Be honest with how much information you may have revealed and how far you (unknowingly )went along with the scam before making the report.
3. Remove your device from the Wifi network
If you're using a Wifi connection, disconnect it immediately because, without the internet, hackers may find it harder to attack other devices or gain more personal information. It can also help prevent a malware attack from spreading to other devices connected to the network.
4. Inform the brand or business Involved
If the hacker used a brand or business name, contact their customer service immediately. Inform them of the details of the scam, so they can carry out an official investigation, recover your funds if they were stolen, and possibly block your account or card to prevent further damage.
How to avoid being phished
- Enable two-factor authentication on your crypto wallet, bank account and social media accounts as well. That extra layer of security can stop the hacker from gaining full access, regardless of how they got your password, pin or other details.
- Always thoroughly research any investment, discount, or giveaway that you come across. Everyone loves a good deal or investment opportunity, so it's easy to fall for a phishing scam that appears to be legit. However, as we mentioned earlier, if it is too good to be true, it isn't.
- Double-check all website links before clicking on them to avoid falling victim to phishing scams. Always scan documents for viruses and malware before downloading or opening them.
- Install anti-phishing and anti-virus software on both personal and work devices. Although cybercriminals are continually cooking up ways to pass through anti-phishing software without detection, the software can still help you avoid standard phishing attempts.
- Always update your security, anti-virus and phishing software to ensure you have the latest phishing blockers and tools.
Final Word
Phishing is a common and dangerous threat to your online security. Cybercriminals are always waiting online to steal your personal information for malicious purposes.
However, you can protect yourself by being as careful as possible. Protect your assets and peace of mind by enabling two-factor authentication, ignoring links and messages from suspicious accounts, and using updated anti-phishing and anti-virus software.
Disclaimer: This article was written to provide guidance and understanding. It is not an exhaustive article and should not be taken as financial advice. Obiex will not be held liable for your investment decisions.
